Secure Key Management in Embedded Systems

Introduction

In an era dominated by digital innovations, the significance of robust
security measures for embedded systems cannot be overstated. Embedded
systems, the heart of countless devices and applications ranging from
consumer electronics to critical infrastructure, require stringent
security protocols to guard against escalating cyber threats. Central to
these security measures is effective key management—a fundamental
aspect that ensures the confidentiality, integrity, and authenticity of
digital communications and data. This white paper delves into the
importance of key management in embedded systems, outlines current
challenges, discusses the consequences of ad hoc key management
practices, and underscores the necessity of managing Hardware Root of
Trust (HRoT) keys.
The Critical Role of Key Management in Embedded Systems
Key
management refers to the administration of cryptographic keys within a
cryptosystem, encompassing their generation, exchange, storage, use, and
replacement. In embedded systems, effective key management is pivotal
for securing device communication and safeguarding sensitive data
against unauthorized access. It serves as the foundation for trust and
security in digital ecosystems, enabling secure boot processes,
encrypted data storage, and secure updates, among other functions.
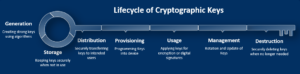
Lifecycle of Key Management: Ensuring Compliance and Minimizing Risks
A
well-defined lifecycle for key management is crucial for maintaining
the security and integrity of embedded systems. This lifecycle
encompasses several critical stages: Generation, Storage, Distribution,
Provisioning, Usage, Management, and finally, Destruction or
Decommissioning. Each stage plays a vital role in ensuring that
cryptographic keys are handled securely throughout their existence.
Generation:
Keys must be generated in a secure manner, using algorithms that ensure
their strength and uniqueness to prevent predictability or duplication.
Storage: Once generated, keys need to be stored securely, with measures in place to protect them from unauthorized access or theft.
Distribution: The process of distributing keys must be secure to ensure that they are not intercepted or tampered with during transit.
Provisioning: Keys must be provisioned to devices or users in a secure manner, ensuring that they are only accessible to authorized entities.
Usage:
The use of keys in operations such as encryption, decryption, signing,
and verification must be managed securely to prevent unauthorized use.
Management: Ongoing management of keys involves monitoring their usage, renewing them as necessary, and ensuring they remain secure.
Destruction or Decommissioning:
Finally, when keys are no longer needed, they must be destroyed or
decommissioned in a manner that ensures they cannot be recovered or
reused.
Managing
this lifecycle effectively is not only essential for maintaining
security but also for ensuring legal compliance. Many regulations and
standards require that cryptographic keys are managed according to
strict guidelines to protect sensitive information and maintain trust. A
well-managed key lifecycle helps prevent the keys from being stolen or
misused, thereby minimizing the risk of data breaches and the associated
legal and reputational consequences. Secure IQx’s solutions streamline
this lifecycle, offering tools and processes that ensure each stage is
handled with the utmost security and efficiency, thereby supporting
companies in meeting their compliance requirements and safeguarding
their assets against threats.
Streamlining Key Management: Addressing Challenges and Emphasizing Solutions
The realm of key management for embedded systems is marked by several pressing challenges that necessitate thoughtful solutions.
- First,
the complexity of managing cryptographic keys across a myriad of
devices and platforms presents a significant hurdle. This complexity is
compounded by the need to secure keys at every phase—from generation and
storage to distribution and usage—against a backdrop of evolving cyber
threats. These threats require continuous updates to cryptographic
algorithms and key management protocols, adding to the operational
burden. - Furthermore, the integration of hardware security
modules (HSMs) and the management of Hardware Root of Trust (HRoT) keys
introduce additional layers of complexity and financial overhead. HRoT
keys are foundational to device security, ensuring secure boot
processes, firmware authentication, and secure communications. Effective
management of these keys is non-negotiable, as it underpins the
device’s defense against unauthorized access and compromises. - The
endeavor to secure embedded devices, such as microcontroller units
(MCUs) and microprocessor units (MPUs), demands a significant and
meticulous effort. Understanding the intricacies of device security is
pivotal for ensuring that foundational processes like secure boot and
firmware updates, particularly over-the-air (OTA) updates, are
impenetrable to threats. This involves a deep dive into the architecture
and capabilities of these devices to implement robust security measures
effectively.
Compliance: The challenges do
not stop at technical and operational complexities. The consequences of
ad hoc or inadequate key management practices are severe. Without a
systematic and secure approach, companies face the risk of data
breaches, compromised device security, and the erosion of consumer
trust. Such outcomes not only entail significant financial repercussions
but also long-lasting reputational damage.
Scalability:
As businesses scale and deploy embedded systems more broadly, the need
for scalable key management solutions becomes critical. Scalability
ensures that security measures grow in tandem with the company, without
leading to prohibitive costs or diminishing security effectiveness. This
scalability is essential for maintaining rigorous security standards,
adhering to global compliance requirements, and managing costs
efficiently.
Real Cost Of KMS: Addressing these
challenges also involves confronting the realities of cost and talent.
Operating an in-house key management infrastructure, including HSM
servers, demands substantial capital and operational investment. The
expenses related to hardware procurement, maintenance, and the physical
infrastructure to support these systems are significant. Moreover, the
specialized nature of key management systems necessitates a skilled
workforce, which is not only hard to find but also expensive to retain.
Secure IQx: A Unified, Cost-effective Solution
Secure
IQx offers an innovative solution to these challenges by providing a
unified, intuitive, and scalable key management system. Designed with
global compliance in mind, Secure IQx’s solutions address the critical
need for cost-effective key management without compromising on security.
By leveraging Secure IQx, companies can significantly reduce the
complexity and expense associated with traditional key management
practices, while ensuring their embedded systems are secured against
evolving threats.
Step into a future defined by unparalleled
security, efficiency, and compliance. Connect with us at
support@secureiqx.com to discover how our partnership can elevate your
security objectives.
Recent Posts
-
Secure Key Management in Embedded Systems
April 16, 2024 Compliance -
Empowering Smart Homes with Matter Compliance
February 21, 2024 Compliance



