The Power of SecureIQx Cloud HSM Server
Securing Your Digital Assets: The Power of SecureIQx Cloud HSM Servers
In an era defined by digital transformation and increasing security threats, safeguarding sensitive data and cryptographic keys has never been more critical. At SecureIQx, we understand the pivotal role that Hardware Security Modules (HSMs) play in fortifying security infrastructures and enabling robust key management practices. Our SecureIQx Cloud HSM servers offer a cutting-edge solution that combines the reliability and scalability of cloud technology with the unparalleled security of HSMs, providing businesses with a powerful tool to protect their digital assets.
The Importance of HSMs in Security Infrastructure
Hardware Security Modules (HSMs) are specialized hardware devices designed to securely generate, store, and manage cryptographic keys, as well as perform cryptographic operations. These devices play a crucial role in ensuring the confidentiality, integrity, and availability of sensitive data, making them a cornerstone of modern security infrastructures.
Benefits of SecureIQx Cloud HSM
1. Scalability: SecureIQx Cloud HSM servers offer unparalleled scalability, allowing businesses to seamlessly scale their cryptographic operations and key management requirements as their needs evolve.
2. High Reliability: Built on top-tier cloud infrastructure, SecureIQx Cloud HSM servers boast exceptional reliability and uptime, ensuring continuous availability of cryptographic services.
3. Global Accessibility: With SecureIQx Cloud HSM, businesses can access cryptographic services from anywhere in the world, enabling seamless collaboration and operation across distributed environments.
Understanding Key Management in Embedded Systems Using Cloud HSM
To provide an example, the diagram below visualizes the process of managing cryptographic keys in embedded systems through the use of a Cloud Hardware Security Module (HSM).
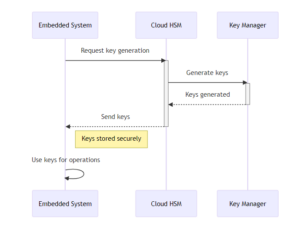
Here’s a step-by-step breakdown:
- Key Request Initiation: The process begins when the embedded system (labeled as ‘E’ in the diagram) requests the generation of cryptographic keys. This is a crucial step for ensuring secure operations within the system.
- Processing the Request: The Cloud HSM (labeled as ‘CHSM’), a dedicated hardware used for managing and safeguarding digital keys, receives this request. The HSM is responsible for the secure generation, storage, and management of these keys.
- Key Generation: Upon receiving the request, the Cloud HSM interacts with a Key Manager (labeled as ‘KM’), which is the component responsible for the actual creation of the keys. This process is securely handled within the cloud environment to prevent unauthorized access or leaks.
- Transmission of Generated Keys: Once the keys are generated, they are securely sent back to the Cloud HSM, which in turn sends them to the embedded system.
- Secure Storage and Usage: The embedded system receives the keys and stores them securely. These keys are then used for various operations that require encryption, such as data storage, communication, or user authentication.
- Note on Security: A note in the diagram emphasizes that the keys are stored securely within the embedded system. This highlights the importance of security in key management processes.
This sequence ensures that cryptographic keys are handled in a secure and efficient manner, leveraging the robustness of cloud-based hardware security modules. Such a system provides a high level of security for embedded systems, crucial in protecting sensitive data and operations.
How SecureIQx Servers Empower Businesses
SecureIQx Cloud HSM servers are the ideal solution for businesses seeking to scale their embedded and hardware HSM requirements. By leveraging our cloud-based infrastructure, organizations can efficiently manage cryptographic keys and perform secure operations at any scale, without the need for significant upfront investment in hardware or maintenance. Our dedicated team of security experts ensures that our Cloud HSM servers adhere to the highest standards of security and compliance, enabling businesses to focus on their core objectives while we handle the complexities of cryptographic key management.
Take Your Security to the Next Level with SecureIQx
In conclusion, SecureIQx Cloud HSM servers offer a powerful solution for businesses looking to enhance their security infrastructure and key management practices. With unmatched scalability, reliability, and global accessibility, our Cloud HSM servers empower organizations to protect their digital assets and mitigate cyber threats effectively. Reach out to SecureIQx today to learn how our Cloud HSM servers can help you scale your embedded and hardware HSM requirements, and take your security to the next level.
Recent Posts
-
Secure Key Management in Embedded Systems
April 16, 2024 Compliance -
Empowering Smart Homes with Matter Compliance
February 21, 2024 Compliance



